Identity Proofing 101: A Practical Guide for Modern Organizations
February 12, 2026
|
Duration:
6
min READ

Introduction
Identity proofing has become a critical control as organizations shift to remote work, digital onboarding, and zero trust architectures. Yet it’s often misunderstood, conflated with authentication, or treated as a one-off compliance task instead of a foundational security capability. This article explains what identity proofing is, how it works, and why it matters across technical, business, and regulatory contexts.
Identity Proofing: The Basics
Q: What’s the difference between identity proofing and authentication from an architecture standpoint?
A: Identity proofing and authentication serve distinct roles. Proofing establishes that a real person matches a claimed identity, typically once, using external verification services, while authentication continuously confirms that the already proofed person is returning. Strong authentication without strong proofing only verifies credential possession, not that the identity-proofed person is returning. proofed person is returning.
Architecturally, modern systems treat proofing as a separate service integrated with the identity provider during onboarding. Proofing providers return an assurance level that’s stored as an identity attribute, enabling access decisions based on how well someone was verified, not just whether they can authenticate.
Q: What methods does identity proofing use?
A: Identity proofing typically layers multiple verification methods, including:
- Document verification
- Database checks
- Biometric matching
- Liveness detection
Q: How does identity proofing use document verification?
A: Document verification validates government-issued IDs. Modern services use machine learning (ML) models trained on thousands of document types to check security features –such as holograms, microprinting, UV patterns, and barcode encoding. These services look for tampering, expired documents, and format inconsistencies. Leading providers maintain updated templates as governments change ID designs. The output is typically a confidence score for document authenticity, along with extracted data (name, DOB, address, document number).
Q: How does identity proofing use database checks?
A: Database checks cross-reference extracted identity data against authoritative sources. These sources include credit bureau header data from Equifax, Experian, and TransUnion; commercial identity graphs; specialty databases such as OFAC watchlists, deceased records, and synthetic identity indicators; and government records where accessible. The goal is to confirm that the identity exists in the real world and that the details are consistent across sources.
Q: How does identity proofing use biometric matching?
A: Biometric matching compares a live capture (selfie or video) against the photo on the identity document. This confirms that the person presenting the document is the person pictured on it. Algorithms generate face embeddings and calculate similarity scores. The key metric is the tradeoff between the False Accept Rate (FAR) and the False Reject Rate (FRR).
Q: What is liveness detection?
A: Liveness detection confirms a real human is present, not a printed photo, video replay, or deepfake. Passive liveness analyzes image characteristics, while active liveness requires the user to perform actions such as blinking, turning their head, or speaking a phrase. This capability helps defend against presentation attacks.
The layers work together. Document verification confirms that a real ID exists. Database checks confirm that the identity is real and consistent across sources. Biometric matching confirms that the person presenting the ID is the person pictured on it. Liveness detection confirms that the person is physically present. Skipping any layer creates a gap that attackers can exploit.
Where Does HR Fit In?
Q: Why should HR care about identity proofing during the hiring process?
A: Remote hiring has created a verification gap that attackers are actively exploiting. Candidates may perform well in interviews but later turn out to be someone else entirely, using proxy interviewers, stolen identities, or deepfakes.
In 2022, the FBI issued a public warning about this risk, citing fake identities used in remote IT interviews for roles with access to sensitive systems. Identity proofing provides a straightforward mitigation. Verifying a government-issued ID at the start of a video interview and confirming that the person on camera matches the document takes only minutes and can prevent proxy interviews altogether.
Q: What are the negative impacts of poor identity proofing during hiring?
A: Failing to validate the identities of new hires can lead to several serious issues, including:
- Wasted hiring investment: Discovering an identity mismatch after onboarding means losing the full cost of recruiting, onboarding, and ramp-up time.
- Legal exposure: In regulated industries, hiring someone who misrepresented their identity can create compliance violations where a verified workforce is required.
- Security risk: Granting network access, email, and potentially sensitive systems to someone whose identity is unverified exposes the organization to significant risk. If the individual is malicious, background checks offer little protection
Q: What’s the business case for identity proofing in workforce onboarding?
A: The average cost of a bad hire is estimated at 30% of an employee’s first-year salary, according to the U.S. Department of Labor. That figure reflects a typical bad hire –caused by poor fit or insufficient skills. When the hire is an imposter or someone using a fraudulent identity, the costs increase significantly and can include:
- Incident response costs when the issue is discovered
- Forensic investigations to determine what systems or data were accessed
- Potential data breach notifications if sensitive information was exposed
- Re-hiring costs to replace the individual with a legitimate employee
- Legal fees and penalties if regulatory requirements were violated
Identity proofing typically costs only $2 to 10 per verification. Without it, unverified employees can gain immediate access to email, systems, and applications. Preventing even a single incident can offset the cost of identity proofing across years of hiring activity.
The Relationship Between Identity Proofing and Compliance
Q: What does NIST 800-63 require for identity proofing?
A: NIST Special Publication 800-63-3 (Digital Identity Guidelines) is the authoritative framework for identity proofing in U.S. federal systems and has become the benchmark across many regulated industries.
The standard is divided into four volumes. For identity proofing specifically, organizations must follow SP 800-63A (Enrollment and Identity Proofing).
NIST defines three Identity Assurance Levels (IALs):
IAL1: No identity proofing is required. The identity is self-asserted and is appropriate only when there is no risk associated with an identity error.
IAL2: Remote or in-person proofing that provides high confidence in the claimed identity. This level requires:
- Collection of identity evidence, typically government-issued IDs
- Validation of evidence authenticity and accuracy
- Verification that the claimed identity belongs to the applicant, using biometric comparison or in-person inspection
- Address confirmation
IAL3: In-person proofing conducted by a trained credential service provider representative, requiring physical presence and direct inspection of identity evidence.
For most enterprise use cases, including workforce onboarding, customer account opening, and access to sensitive systems, IAL2 is the recommended target. It provides strong assurance while remaining achievable through remote and automated processes.
The key compliance consideration with NIST 800-63, is not only whether identities are proofed, but how thoroughly they are proofed and whether the process can be demonstrated. Auditors typically expect documented proofing procedures, records of evidence collection, and validation of results.
Q: What industries have regulatory requirements for identity proofing?
A: Identity proofing requirements show up across multiple regulatory frameworks. Here’s where you’ll run into explicit or implied mandates:
- Financial services
- Healthcare
- Federal government and contractors
- Critical Infrastructure
Q: What are the regulatory requirements for financial services organizations?
A: The Bank Secrecy Act (BSA) and its implementing regulations require financial institutions to maintain Customer Identification Programs (CIP) under 31 CFR §1020.220. These programs mandate risk-based identity verification using documentary and non-documentary methods to establish a reasonable belief that the institution knows the true identity of each customer. Financial Crimes Enforcement Network (FinCEN) guidance further clarifies acceptable verification procedures. Customer identification is a foundational element of broader BSA/AML (Anti-Money Laundering) programs, which also require ongoing monitoring and reporting.
Q: What regulations do healthcare institutions need to comply with?
A: HIPAA doesn’t explicitly mandate identity proofing, but the Security Rule’s access control requirements under 45 CFR §164.312 effectively require it for workforce members who access electronic protected health information (ePHI). In addition, for the e-prescribing of controlled substances, the DEA’s EPCS regulations under 21 CFR §1311 explicitly require identity proofing to standards equivalent to NIST IAL2 before prescribing credentials are issued.
Q: What regulations must federal agencies and government contractors meet?
A: Federal agencies are governed by Office of Management and Budget (OMB) guidance that establishes government-wide digital identity and access requirements. OMB Memorandum M-04-04 established the e-authentication guidance, and subsequent directives, including M-19-17, require federal agencies to implement digital identity practices aligned with NIST Special Publication 800-63. Federal contractors that handle Controlled Unclassified Information (CUI) must meet security and identity requirements under NIST 800-171, which defines identification and authentication controls for non-federal systems. For Department of Defense contractors, these requirements are enforced through the Cybersecurity Maturity Model Certification (CMMC) program.
Q: What regulations do critical infrastructure organizations need to comply with?
A: Critical infrastructure organizations, including those in energy, transportation, and other regulated sectors, must comply with industry-specific standards. In the energy sector, NERC Critical Infrastructure Protection (CIP) standards require personnel risk assessments for individuals with authorized access to critical cyber assets. While these standards are not prescriptive about specific identity proofing methods, they clearly require identity verification as part of access authorization and ongoing risk management.
The common thread across critical infrastructure regulations is the need to clearly establish who has access to regulated data and systems. Meeting this requirement requires more than accepting a self-asserted identity and instead relies on verifiable, documented identity assurance.
Putting Identity Proofing into Practice
Q: How does identity proofing fit into workforce onboarding workflows?
A: Identity proofing integrates into existing HR and IT systems as part of the onboarding lifecycle. A typical workflow looks like this:
- Pre-boarding (after offer acceptance): The candidate receives a secure link to complete identity verification. They capture a photo of a government-issued ID and a selfie. Behind the scenes, the identity proofing service validates the document, runs database checks, and performs biometric matching. This process is typically completed in minutes.
- HR system integration: Proofing results flow into your HRIS of record, such as Workday or SAP SuccessFactors, as part of the new hire profile. The proofing event is logged with a timestamp, the assurance level achieved, and the verification outcome, creating a documented compliance record.
- Identity provider binding: When IT provisions the employee’s digital identity in the IdP, such as Microsoft Entra ID or Okta, the proofing assurance level is stored as an identity attribute. This enables downstream access policies to be based on how thoroughly the individual was verified, not just whether they can authenticate.
- Privileged access requests: If the employee later requests elevated access, such as admin privileges, financial systems, or sensitive data, re-proofing can be required as a step-up control. The original proofing result establishes a baseline, while re-proofing confirms the individual’s identity before granting additional access.
Q: Why isn’t a background check enough? Why do I need identity proofing, too?
A: A common question with a simple answer is that a background check performed on an unverified identity is likely to return the wrong person.
Background checks provide information about someone’s history, including criminal records, employment verification, education, and credit. However, they assume the claimed identity is legitimate. If an individual applies using a stolen or synthetic identity, the background check may come back clean because it’s validating the fabricated persona, not the actual human being.
The correct sequence matters:
- Identity proofing first: Verify that the person is who they claim to be
- Background check second: Evaluate the verified individual’s history
Skipping identity proofing makes the background check unreliable and significantly reduces its value.
Q: What happens if we don’t implement identity proofing?
A: Identity proofing typically costs only single-digit dollars per verification. The cost of not implementing proofing is far higher and is measured in incident response, regulatory penalties, and long-term recovery.
The risks include:
- Fraud exposure: Without identity proofing, organizations rely on self-asserted identities. That trust is routinely exploited through fake identities in customer onboarding or proxy interviews during hiring, as attackers follow the path of least resistance.
- Compliance gaps: In regulated industries, weak or undocumented identity verification often results in audit findings. Regulators expect evidence of formal identity verification procedures, not informal or ad hoc checks.
- Incident costs: According to the Ponemon Institute’s 2023 Cost of a Data Breach report, the average cost of a data breach in the United States reached $9.48 million. Insider-related incidents are among the most difficult to detect and the most damaging, making identity proofing low-cost risk insurance.
- Reputational damage: Discovering that an employee or contractor was operating under a false identity can severely damage customer trust, attract negative press, and make future hiring more difficult.
Q: How do we determine the level of identity proofing we need?
A: The right approach is to match the level of identity assurance to the level of risk. Not every access scenario requires the same degree of proofing.
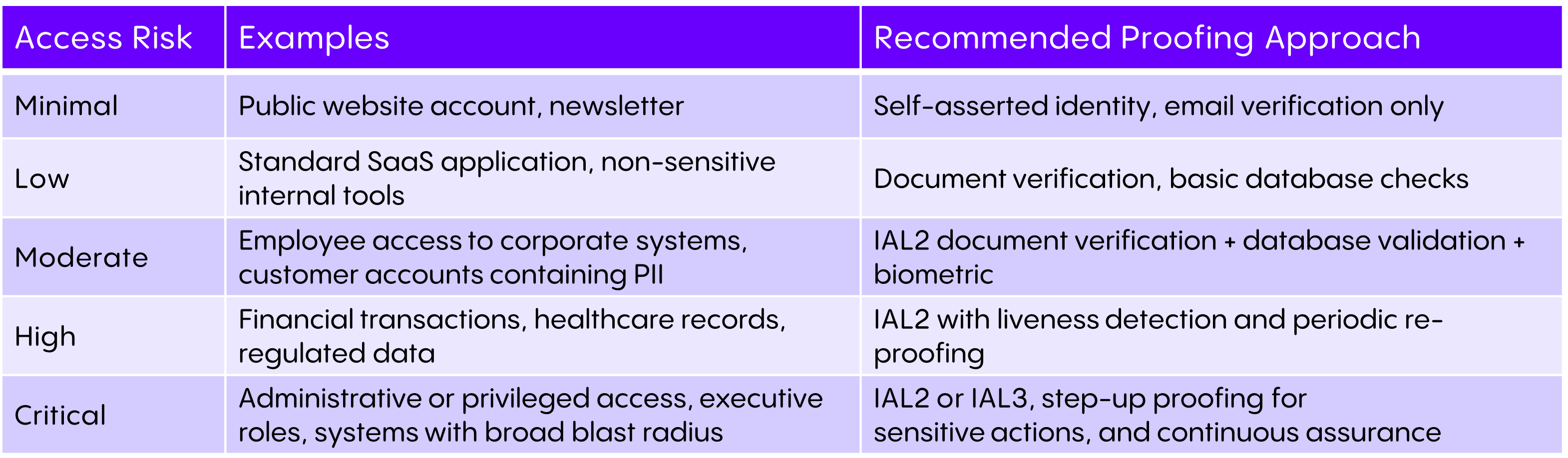
The principle is straightforward. Over-proofing low-risk access adds cost and friction, while under-proofing high-risk access creates significant exposure. Organizations should map access types to risk tiers and apply controls accordingly.
An orchestration-based approach allows proofing requirements to adapt over time without brittle, point-to-point integrations. For organizations that need a formal, auditable framework, NIST SP 800-63-3 Section 5 (Digital Identity Risk Management) provides a structured methodology for aligning proofing levels to risk and documenting compliance.
Q: Why are traditional help desk verification methods insufficient?
A: The help desk is one of the most common targets for social engineering attacks. An attacker calls in, claims to be an employee who is locked out, and persuades a well-meaning support technician to reset credentials. Once that happens, the attacker gains legitimate access.
A well-known example is the 2023 MGM Resorts breach, which began with a phone call to the help desk. Attackers used information gathered from LinkedIn to impersonate an employee and convince support staff to reset credentials. The incident resulted in widespread operational disruption and an estimated $100 million in damages.
Traditional help desk verification methods are ineffective because:
- Knowledge-based questions such as employee ID numbers or manager names can be easily researched or socially engineered
- Callbacks to phone number on file add friction but can be bypassed if an attacker has compromised the employee’s device or updated directory information
- Manager approval introduces delays and still relies on human judgement, which can be exploited if the manage cannot reliably verify the requester
These approaches verify familiarity, not identity, making them insufficient defenses against modern social engineering attacks.
Q: How can identity proofing help secure help desk interactions like password resets?
A: Identity proofing adds a layer of verification that is difficult to fake. When someone contacts the help desk for a password reset or privileged access, support staff can trigger a identity proofing step. The requester receives a secure link on their mobile device, verifies a government-issued ID, and completes a biometric match. The help desk receives confirmation that the person requesting access matches the identity on file before taking action.
This approach is especially effective for high-risk requests, including:
- Password resets for privileged accounts
- MFA resets, which are a common attack vector because they bypass existing authentication controls
- Access requests for sensitive systems or data
- Requests that are unusual or out of pattern for the user
For legitimate users, the added friction is minimal and typically takes only a minute or two. For attackers, the barrier is significant, as they cannot complete the process without the target’s physical presence and identity. By applying stronger proofing only to higher-risk scenarios, organizations can balance security with operational efficiency through tiered verification.
Getting started with MajorKey’s IDProof+
Q: What’s a good starting point for adding identity proofing to our security strategy?
A: A strong starting point is IDProof+, a rapidly deployable identity assurance solution built in collaboration with authID and integrated with Microsoft Entra Verified ID. IDProof+verifies identities using government‑issued IDs and biometric matching, enabling organizations to confidently hire, onboard, and support remote users while strengthening overall identity assurance.
Want to learn more? Book a customized IDProof+ demo to see how it fits into your environment.
Authors

Workforce Identity
Advisory
Deployment and Integration
No items found.
.svg)



















.svg)
