Have You Solved Your IAM Problem?
January 8, 2026
|
Duration:
7
min READ

Struggling to make sense of your IAM ecosystem? Discover how to overcome tool overload, achieve continuous reliability, and align identity management with business outcomes. In this blog, you'll learn practical strategies for visibility, observability, intelligence, and action - plus insights on AI’s impact in modern IAM.
Introduction: The IAM Tool Overload
If you ask any IAM leader today, you’ll likely hear: “We have too many tools.” Many overlap in features and functions, some are rarely used, while others are essential. Yet, an abundance of tools doesn’t guarantee the outcomes organizations need.
Self-Assessment: Key Questions for Your IAM Ecosystem
To determine if you’ve truly solved your IAM problem, consider these questions about your tools, processes, and overall ecosystem:
- Are you aware of all the tools you’ve deployed, purchased, or have sitting unused?
- Do you have a comprehensive view of your IAM ecosystem - beyond just tools and technology?
- Can you see all aspects of your organization’s IAM attributes?
- Where do you turn when you need to dig deeper (e.g., debugging, forensics, or incident response)?
- Do you have actionable information when you need it?
- Are you able to take actions automatically, or must you rely on manual processes?
- Can you rely on your systems to “continuously” to provide reliable information and outcomes?
- Most importantly, are your systems working in an integrated way, or are they operating in silos?
The IVIP Framework: Reducing IAM Risk
In its 2025 Hype Cycle™ for Digital Identity, Gartner® introduced the concept of Identity Visibility and Intelligence Platforms (IVIP). As per the report:
“Identity visibility and intelligence platforms are products that provide rapid integration and visibility for identity and access management (IAM) relevant data, typically paired with advanced analytics (often AI-enabled) capabilities. This innovation provides a single view of IAM data, activity/events, relationships, configuration and posture to enable rapid improvement of all other integrated IAM controls and capabilities supporting both improved security and business enablement.” 1
To reduce the attack surface caused by IAM shortcomings, organizations should ensure their IAM environment possess these attributes:
- Visibility: Unified, just-in-time information.
- Observability: Continuous, reliable monitoring relevant activities.
- Intelligence: Correlation of discrete events to inform decisions and proactive orchestration.
- Action: Automated responses based on intelligence from visibility and observability.
MajorKey was recognized in the AM/IGA/PAM Augmentation section of Gartner’s graphic in the 2025 Gartner report, “Reduce Your IAM Attack Surface Using Visibility, Observability, and Remediation” by Rebecca Archambault (8 October 2025). To learn more, read the full report here.
Strategic Technology Use: Maximizing What You Have
The solution isn’t adding more technology to your already complex IAM landscape. Instead, ask your vendors how they support visibility, observability, intelligence, and actionability. If these aren't provided natively, determine what’s needed to achieve them.
Key points for organizations:
- Strive for optimal utilization of the tools and technologies you have already invested in, deployed, and developed skillsets for.
- Focus on business outcomes, not just vendor promises or shiny features.
- Optimize and act on what’s relevant to your business—automated or manual.
MajorKey Positioning
At MajorKey, we’ve seen organizations struggle with the lack of clear direction for strategically positioning IAM investments. Common challenges include misalignment between IAM initiatives and business objectives, difficulty demonstrating ROI, and an over-reliance on technology without a cohesive strategy. In our experience, these issues often lead to fragmented IAM ecosystems and missed opportunities for business value.
To address these challenges, MajorKey partners with organizations to:
- Assess current IAM maturity and alignment with business goals
- Develop strategic roadmaps that prioritize outcomes over tools
- Facilitate stakeholder engagement to build internal champions
- Establish metrics for measuring IAM success and impact
- By taking a business-centric approach, we help clients untangle complexity and ensure IAM investments deliver meaningful results.
IAM investments should demonstrate relevant business outcomes, identify internal champions, and simplify the complexity created by numerous technology acquisitions.
Shifting to a Business-Centric Approach
A tech-centric approach can quickly become a business-centric dilemma. Security and IAM leaders who made short-term decisions are now being asked for long-term strategies and continuous demonstration of value and ROI.
How do we help? Historically, we provided IAM consulting through business outcome-centric advisory services, advanced engineering, and progress-oriented managed operations. We also focused on bridging gaps created by technology-centric approaches.
Over the years, we’ve developed products and accelerators that help organizations increase visibility and observability, act intelligently based on advanced analytics, and automate capabilities. The following diagram summarizes our systematic and modularized approach.
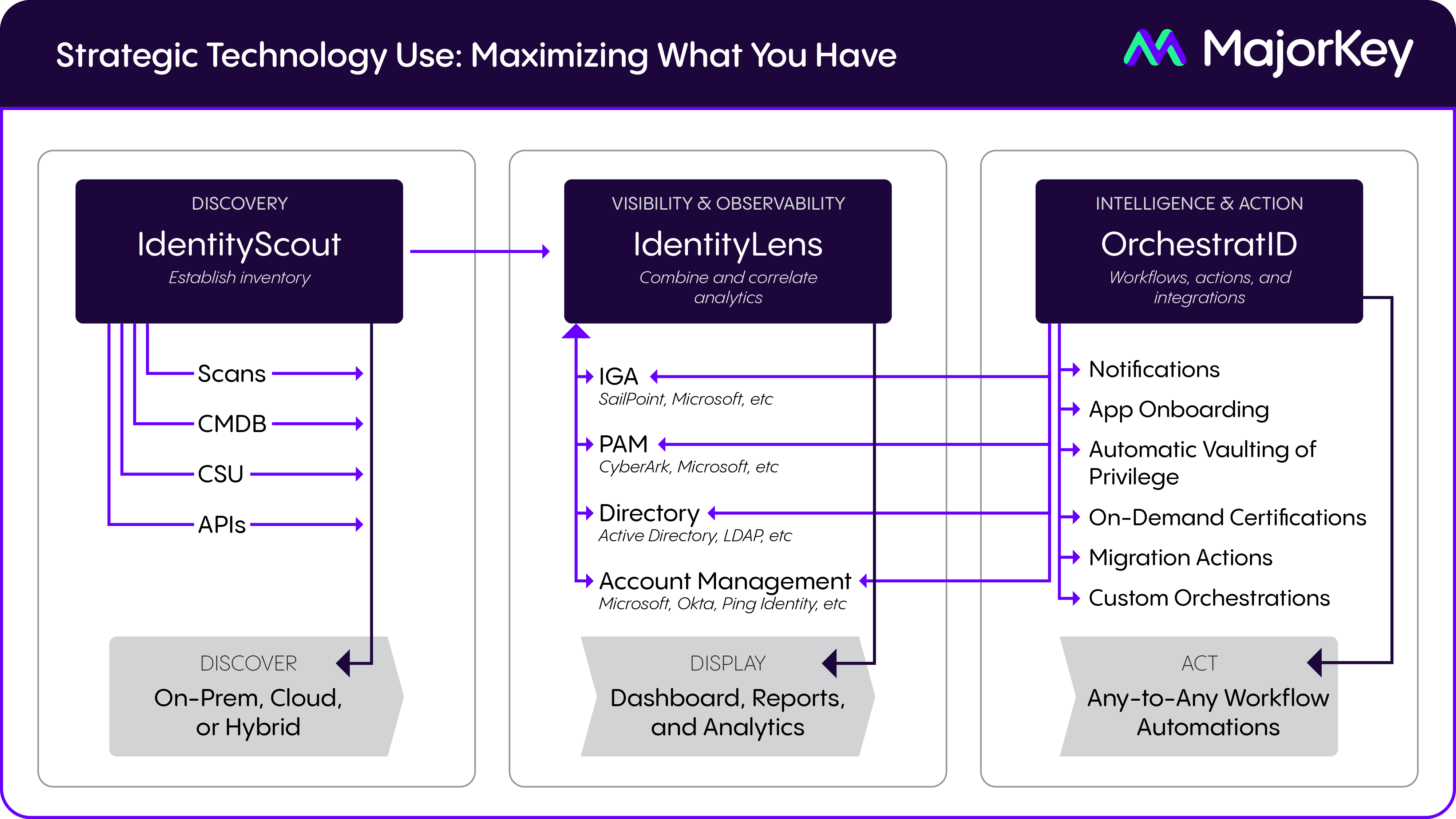
The Impact of AI in Modern IAM
While addressing IAM gaps with innovative approaches, we must not overlook the impact of AI in modern IAM.
- Product vendors are racing to enrich their offerings with AI-powered features.
- Organizations are adopting AI for business benefits, with some taking a bold “AI-first” approach.
- Common questions include: What should our AI strategy for IAM be?
Organizations are struggling with:
- Are we adopting AI in the right way?
- Are we doing enough?
- Do we have the right focus and investments?
- Are we missing out (FOMO)?
Actionable Advice for IAM Leaders
- Are your IAM objectives aligned with your business outcomes?
- Have you addressed gaps in visualization?
- Are you able to make intelligent decisions to automate relevant actions?
- Can AI help in any or all of the above?
- Do you have the right representation in your organization’s AI working group?
AI or No AI:
When addressing your IAM gaps, focus on the fundamentals. Start with business outcomes and organizational champions. Ensure continuous access to reliable identity data. Establish a collaborative, not siloed, identity ecosystem. Foundationally, address "who has access to what" - be it human, non-human or agents
Moving Forward with Confidence in IAM
Solving your IAM problem isn’t just about technology - it’s about clarity, strategy, and continuous improvement. By focusing on visibility, intelligence, and business outcomes, organizations can untangle complexity and reduce risk. Whether you’re leveraging AI or optimizing existing tools, the path forward requires collaboration, adaptability, and a commitment to aligning IAM with your business’s evolving needs.
At MajorKey, we’re here to help you turn IAM challenges into opportunities for growth and resilience. Ready to take the next step? Assess your IAM ecosystem, engage your champions, and let’s build a secure, business-centric future together.
Frequently Asked Questions (FAQs)
1. What is Identity and Access Management (IAM)?
Identity and Access Management (IAM) refers to the processes and technologies used to manage digital identities and control user access to resources within an organization. Effective IAM ensures that the right individuals have the appropriate access at the right times.
2. Why do organizations struggle with too many IAM tools?
Many organizations accumulate multiple IAM tools over time, leading to overlapping features, unused capabilities, and increased complexity. This tool overload can hinder visibility, integration, and business outcomes.
3. What does IVIP stand for, and why is it important in IAM?
IVIP stands for “Identity Visibility and Intelligence Platforms.” This term, introduced by Gartner, refers to solutions that unify identity data, activity, relationships, and security posture across an organization’s digital ecosystem. IVIP platforms help organizations gain a comprehensive, real-time view of who has access to what, enabling smarter decisions, reducing risk, and supporting compliance. By providing unified visibility and actionable intelligence, IVIP is becoming essential for modern identity and access management strategies.
4. What are the key attributes of a successful IAM environment?
According to Gartner’s IVIP framework, a robust IAM environment should provide:
- Visibility: Unified, real-time information
- Observability: Continuous monitoring of activities
- Intelligence: Correlation of events for informed decisions
- Action: Automated responses based on insights
5. How can organizations maximize their existing IAM investments?
Focus on optimizing current tools and technologies, aligning IAM objectives with business outcomes, and leveraging vendor capabilities for visibility, observability, intelligence, and actionability. Avoid adding unnecessary platforms and prioritize integration.
6. What role does AI play in modern IAM?
AI is transforming IAM by enabling smarter analytics, automation, and decision-making. Organizations are adopting AI-driven features to enhance security, streamline operations, and address gaps in traditional IAM approaches.
7. How do I know if my IAM strategy is effective?
Ask yourself:
- Are IAM objectives aligned with business outcomes?
- Do you have actionable, reliable identity data?
- Are you able to automate relevant actions?
- Is your IAM ecosystem collaborative and integrated?
8. What are common pitfalls in IAM implementation?
Common challenges include lack of stakeholder alignment, unclear objectives, tool overload, and failure to integrate IAM with broader business strategies. Regular reviews and continuous improvement are essential for success.
1 Gartner, Hype Cycle for Digital Identity, 2025, Nayara Sangiorgio, Nathan Harris, 14 July 2025
GARTNER and HYPE CYCLE are trademarks of Gartner, Inc. and/or its affiliates. Gartner does not endorse any company, vendor, product or service depicted in its publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner publications consist of the opinions of Gartner’s business and technology insights organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this publication, including any warranties of merchantability or fitness for a particular purpose.[
Authors

Workforce Identity
Privileged Identity
Identity Governance
Advisory
Deployment and Integration
No items found.
.svg)



















.svg)
