Securing Modern Identities: How Microsoft Entra ID Governance Transforms Access Management
November 21, 2025
|
Duration:
6
min READ

Part 1 of this series explores the current MIM landscape and options for moving to the cloud. In this second installment of our Transitioning Beyond MIM Revisited series, we explore governance as it relates to identity—specifically, Microsoft Entra’s rapidly evolving capabilities and their impact on organizations navigating the shift from MIM.
What is Identity Governance?
Identity governance ensures that the right people have the right access at the right time—and that organizations can prove it. A strong governance strategy should answer:
- Which users should have access to which resources?
- What are those users doing with that access?
- Are there effective controls for managing access?
- Can auditors verify that those controls work?
Operational efficiency is critical—governance controls must not hinder productivity or inflate audit costs.
Why Microsoft Entra ID Governance Matters
Microsoft Entra ID Governance has introduced powerful advancements that can transform your approach to identity governance and accelerate the transition away from legacy solutions like MIM. Key capabilities include:
- Identity Lifecyle Management
- Dynamic Groups
- Access Reviews
- Entitlement Management
- External Identities
Let’s take a closer look at each one.
Identity Lifecycle Management (ILM)
Microsoft Entra ID Governance delivers modern ILM features:
- HR-driven provisioning (Workday, SuccessFactors) for Microsoft Entra and on-premises AD accounts.
- Automated app provisioning for pre-integrated applications (gallery SaaS apps like ServiceNow and Drop Box) and SCIM 2.0-enabled apps.
- On-premises application provisioning for SQL databases, LDAP directories, and flat files.
While some scenarios still require MIM, its role is shrinking as cloud-first identity management takes center stage.
Dynamic Groups
Dynamic groups play a critical role in audits and control verification, making them a cornerstone of identity governance. Microsoft Entra ID Dynamic Groups work well in cloud-centric environments and now support on-premises Active Directory groups by designating Entra ID as the source of authority (SOA). This enables Entra ID Dynamic Groups to provision access to on-premises groups that were previously managed locally.
MIM still adds value by structuring identities and synchronizing on-premises AD accounts to Microsoft Entra ID via Entra Connect. It also provides attribute values that dynamic groups use to populate memberships, such as licensing groups, SaaS app access, and Azure role assignments.
Because governance for dynamic groups can be complex, recommendations follow a thorough analysis of business requirements. Options include retaining MIM, adopting Entra ID groups as the SOA, leveraging SCIM connectors, or implementing third-party ISV solutions. We expect Microsoft to introduce additional capabilities in this area over time.
Access Reviews
Microsoft Entra ID continues to evolve rapidly, particularly in areas like access reviews and separation of duties (SoD). When combined with Azure Audit Logs, Microsoft Entra ID delivers the data organizations need for successful audits. This is a fast-moving space for Microsoft, with significant changes expected in both the near term (within six months) and long-term.
When necessary, both MIM and Entra ID SOA for groups can manage the creation and administration of on-premises AD groups. Now, access reviews can be implemented to ensure the right people maintain appropriate memberships—across both on-premises groups and Microsoft Entra ID.
Entitlement Management
On-premises synchronized Microsoft Entra ID accounts can enable users to request additional access to Azure Resources, such as licensing groups, SaaS applications, and Azure Role assignments. Entitlement Management manages the identity and access lifecycle by automating access request workflows, access assignments, reviews, and expiration.
External Identities
Organizations have traditionally relied on MIM to manage external users by creating on-premises accounts for resource access. This approach lacks a definitive source of truth and often leaves accounts active indefinitely. Microsoft Entra ID Governance solves this challenge with robust controls, including:
- Onboarding external users through an approval process and managing their lifecycle with access packages. When a package expires, the user is automatically removed from Azure.
- Conducting access reviews to disable or delete external identities that are no longer required.
- Identifying manually created external accounts that were not invited through an Entitlement Management process.
Privileged Identity Management
Microsoft Entra ID Privileged Identity Management (PIM) reduces the risk of excessive or misused permissions by enabling time-based and approval-based role activation for sensitive resources. Currently, PIM is available only for Azure resources.
For organizations with on-premises privileged groups, Azure PIM can manage these groups using custom write-back scripts—an alternative to investing in the MIM PAM solution. Microsoft is expected to deliver more built-in Azure processes for managing on-premises groups in the future.
Azure PIM also supports guest user management by allowing administrators to:
- Assign access to specific Azure resources
- Set assignment durations and end dates
- Enforce two-step verification during activation
This functionality can replace MIM’s traditional on-premises account solution for external users.
While MIM offers its own Privileged Access Management (PAM) solution for on-premises Active Directory, this approach is no longer recommended. Designed for isolated environments, MIM PAM is incompatible with modern applications and zero-trust frameworks.
HorizonID
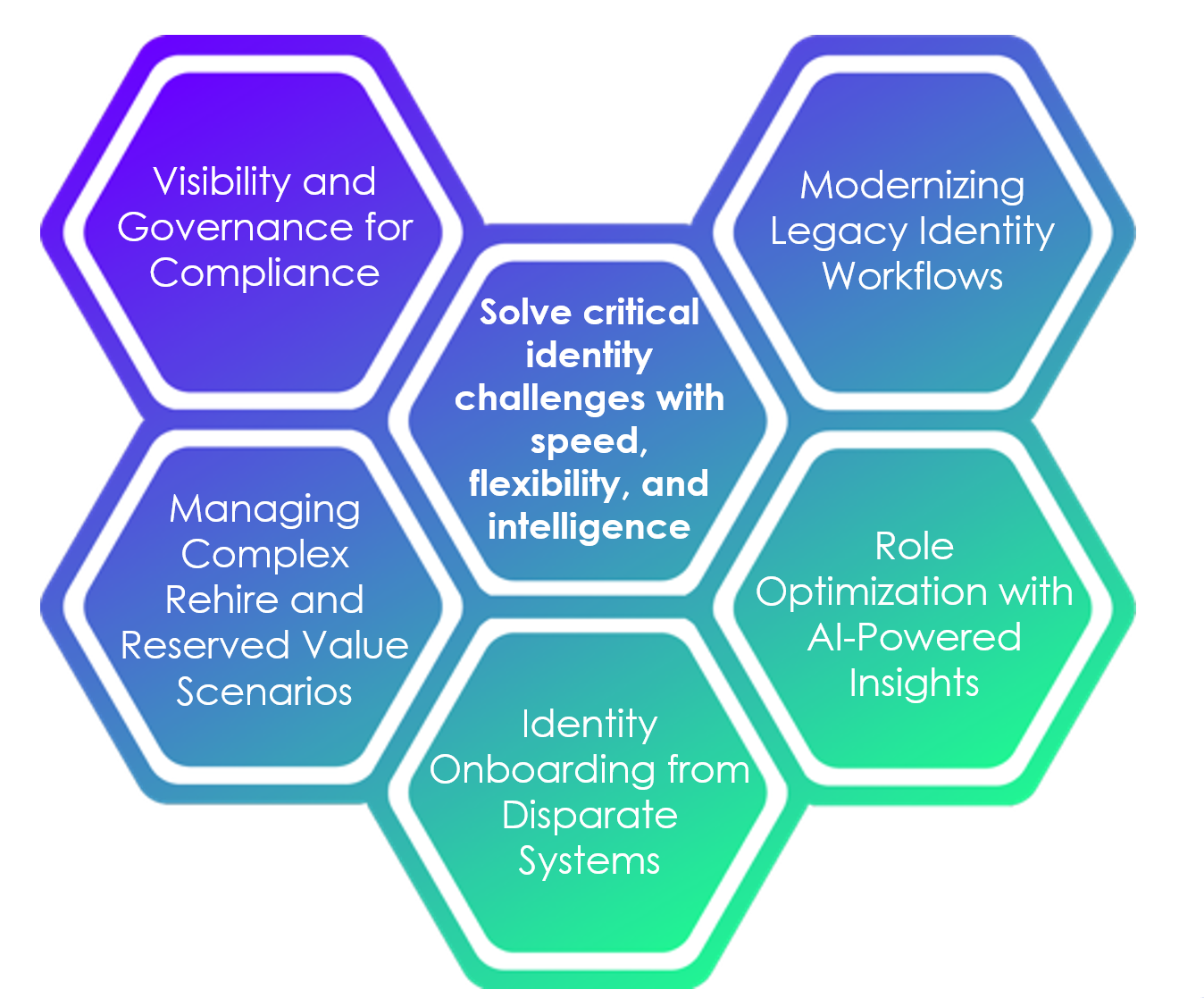
Transitioning to a modern identity platform like Microsoft Entra Suite can be complex, and many organizations encounter roadblocks like brittle legacy workflows, disparate systems, complicated reserve value scenarios, and a lack of visibility that make migrations seem daunting. The good news: with a clear strategy and the right tools, modernization is absolutely achievable.
MajorKey helps organizations overcome these challenges with our powerful extension solution, HorizonID. Designed to enhance Microsoft Entra ID Governance, HorizonID enables a seamless transition of custom line-of-business integrations—unlocking the full value of your Microsoft Entra investment. From legacy integrations to complex workflows to conflicting data across sources, HorizonID removes obstacles and simplifies migrations.
Key Capabilities of HorizonID
Conclusion
Modern identity governance is evolving rapidly, and Microsoft Entra ID is at the forefront with powerful capabilities that streamline lifecycle management, strengthen access controls, and reduce reliance on legacy solutions like MIM. While a full transition may require careful planning and hybrid approaches, organizations now have more tools than ever to secure identities, simplify compliance, and embrace zero-trust principles. With innovations like dynamic groups, entitlement management, and PIM, the future of identity governance promises greater efficiency, stronger security, and a clear path to modernization.
Ready to take the next step? Explore Microsoft Entra ID and see how solutions like HorizonID can help you overcome migration challenges and unlock the full potential of your identity strategy.
- Learn more about HorizonID
- Request a free MIM migration consultation with an identity expert
Frequently Asked Questions (FAQs)
What is Identity Lifecycle Management (ILM)?
ILM is the process of creating, managing, and removing user identities and their access privileges to resources and applications throughout an organization’s environment. It encompasses onboarding new users, updating access as roles or attributes change, and deprovisioning accounts when users leave. A well-defined and streamlined ILM process is crucial for security and efficiency, as poor ILM can lead to productivity issues and security gaps by improperly managed accounts.
What are Dynamic Groups?
Dynamic groups are a key component of identity governance, automating membership based on user or device attributes (e.g., job title, department or location). When attributes change, such as a promotion or relocation, users are automatically added or removed from the appropriate dynamic groups.
This ensures users have the right access when needed and lose it promptly when roles change or employment ends.
What are Access Reviews?
Access reviews periodically verify and recertify user access to resources like groups, applications, and roles. They help maintain compliance and improve security by reducing excessive or outdated permissions.
Access reviews enable organizations to:
- Ensure new employees have the access they need to be productive
- Remove outdated or unnecessary access as roles change roles or employees leave
- Regularly review guest user access
- Improve audit results and reduce risk of compromise
What is Privileged Identity Management (PIM)?
PIM minimizes the risk of excessive or misused permissions by enforcing least privilege principles. It provides time-based, approval-based, and just-in-time role activation for sensitive roles, eliminating permanent admin access.
Key capabilities to strengthen security posture and compliance include:
- Justification, multifactor authentication (MFA), and approval for elevated roles
- Continuous access monitoring
- Scheduled access reviews
- Detailed auditing of privileged activity.
What is HorizonID?
HorizonID is MajorKey’s extension solution designed to simplify and accelerate migration from legacy identity systems to Microsoft Entra ID Governance or Microsoft Entra Suite. It addresses common challenges like fragmented data, complex workflows, and custom integrations. Core capabilities include:
- Advanced identity onboarding from multiple systems
- Streamlined onboarding and offboarding processes
- Duplicate prevention for rehire scenarios
- Unified visibility through a cloud metaverse with custom reporting
- AI-powered insights for role optimization and smart role mining
Authors

Identity Governance
Advisory
Deployment and Integration
No items found.
.svg)



















.svg)
