From Shadow to Certainty: Securing Machine Identities with Confidence (2025 Navigate Session Recap)
October 16, 2025
|
Duration:
6
min READ

One of the biggest themes at this year’s SailPoint Navigate was the explosive growth of machine identities. With machines now outnumbering humans by staggering ratios, unmanaged identities have become a critical, and often overlooked, attack vector that organizations can no longer afford to ignore.
We explored this topic during our session, “From Shadow to Certainty: Securing Machine Identities with Confidence,” presented by MajorKey’s Director of IAM Services, Phil Martinez. If you weren’t able to attend live, keep reading to discover why machine identities are critical, the risks they pose, and how to secure them with confidence.
The Machine Identity Explosion
Machine identities, such as service accounts, API tokens, containers, and more, are the fastest growing identity management segment. Gartner estimates machines outnumber humans by a staggering 45:1, and nearly half of organizations experienced breaches linked to compromised machine identities last year. In 2024 alone, over 39 million secrets were leaked on GitHub, with high-profile incidents at companies like Microsoft and T-Mobile underscoring the urgency for proactive machine identity security.
Legacy vs. Modern Identities
Legacy identities are static and manual, relying on stored secrets and broad access. Modern identities are dynamic, ephemeral, and policy-driven, leveraging just-in-time (JIT) credentials and automated lifecycles. Moving from legacy to modern reduces risk and aligns with zero trust principles.
Legacy Machine Identities
- Static, manual, predictable
- Stored secrets (passwords, API tokens)
- Broad, persistent access across services
- Manual lifecycle; weak ownership
- Examples:
- AD Service Account - Static password, manual rotation
- Entra App Registration with a Client Secret - Long-lived secret requiring manual management
- A Salesforce integration user with a static API security token - Static, non-expiring token requiring manual management
Modern Machine Identities
- Dynamic, automated, intelligent
- No stored secrets (JIT tokens, OAuth)
- Tightly scoped to workload & time window
- Examples:
- AWS IAM Roles for ECS Tasks - Ephemeral, automatically rotated credentials
- Microsoft Entra ID Managed Identity - Passwordless and managed by Entra, eliminating stored secrets.
- Okta API Access Management with OAuth 2.0 – Short-lived, scoped tokens via a standard OAuth 2.0 flow
Governance Gaps and Attack Paths
In traditional workforce identity management, responsibilities are fairly linear: Human resources manages people and lifecycle events, Security oversees policies and controls, and IAM teams handle access and governance. This structure works well for human identities, but machine identities shatter this mold.
With machine identities, accountability becomes fragmented. DevOps, IAM, Security, and Platform teams all play a role, yet ownership is often unclear. A common pattern we see:
- A developer creates a service account for a sprint
- The feature ships and the team moves on
- The account persists with broad privileges
- No deprovisioning or credential rotation takes place
The result? Unmanaged, over-privileged identities lingering across your environment. Overprovisioning compounds this problem, as teams grant broad access for convenience and rarely revisit permissions. This accountability gap poses a serious risk, and demands a more collaborative, cross-functional approach to identity governance.
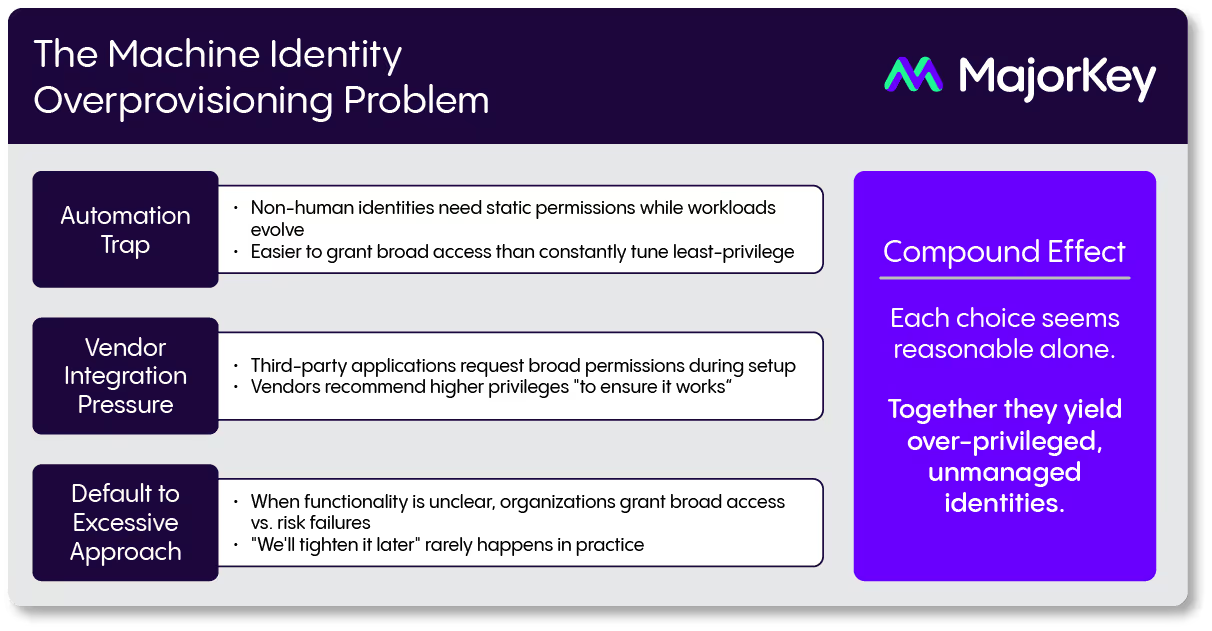
Revealing Hidden Attack Paths
Traditional identity tools often fall short when it comes to uncovering the attack paths created by machine identities. For example, a user owning a service principal can add secrets, bypass MFA, and escalate privileges to Global Admin. These ownership relationships are frequently missed during certification campaigns, leaving dangerous blind spots for attackers to exploit.
Tools like Bloodhound can help uncover these hidden paths—surfacing risks that traditional reviews often overlook and giving security teams the visibility they need to take action.
From Discovery to Governance
Discovery alone isn’t enough; it’s just the beginning. To truly secure machine identities, organizations need automated classification, AI-powered detection, and seamless integration with governance workflows. Solutions like SailPoint’s Machine Identity Security go beyond visibility, helping group machine accounts by business applications, assign clear ownership, and feed into certification workflows.
Core features include:
- Automated Discovery and Classification: Discover and classify machine accounts across Active Directory, Entra ID, and cloud platforms
- AI-Powered Detection: Identify potential machine identities by flagging naming patterns like "service" or "svc"
- Smart Filtering: Find accounts with no human association or those with risky attributes, such as passwords that never expire
Actionable Strategies for Security Machine Identities
- Start With Cross-Functional Coordination: Establish dedicated Machine IAM working groups that bring together IAM, Security, DevOps, and Platform teams to align ownership and accountability
- Implement Policy-As-Code Enforcement: Deploy CI/CD pipeline gates that automatically detect and block static credentials before deployment, preventing risky configurations from reaching production
- Enable Continuous Certification: Move beyond calendar-based reviews. Trigger access reviews based on real-time events like privilege changes, credential additions, and unused permissions
- Activate AI-Driven Monitoring: Turn on anomaly detection for privileged service accounts and workload identities to catch suspicious behavior before it escalates
- Quick Win Example: Migrate kerberoastable service accounts to Group Managed Service Accounts (gMSA) to enable automatic 30-day password rotation and reduce credential exposure
Final Thoughts: Why Machine Identity Security Can’t Wait
Machine identities are multiplying, and so are the risks. The path forward requires more than technical fixes; it demands a strategic transformation. That means eliminating static credentials, embracing ephemeral identities, and embedding Zero Trust principles into every layer of your infrastructure. Continuous governance and AI-driven risk detection aren’t just best practices - they’re quickly becoming the standard.
This isn’t just a technical challenge. It’s an organizational imperative. Now is the time to align cross-functional teams, modernize identity workflows, and embed security into your development lifecycle from the start.
What to dive deeper?
Authors

No items found.
No items found.
No items found.
.svg)



















.svg)
